Get a New Computer’s Auto Pilot Hash Without Going Through the Out of Box Experience (OOBE)
Follow up: With windows 11 – this can be done by default in a couple steps: https://learn.microsoft.com/en-us/mem/autopilot/add-devices#diagnostics-page-hash-export
With Auto Pilot you need to import a machines Auto Pilot hash, or hardware ID, to register the device with the Windows Auto Pilot deployment service in Azure. Ideally, the process of getting the Auto Pilot hash would be performed by the OEM, or reseller from which the devices were purchased, but currently the list over participating resellers is small. The other option is to do it manually which requires you boot the device up, go through the out of box experience (OOBE), and then run a PowerShell script which will spit out the hash CSV for you to then import into Auto Pilot. This process can be time consuming if you have a batch of new machines, and once you get the hash for each device, you must reset it so during the next boot it will go through the OOBE and enroll via Auto Pilot.
In this post I will show you how you can grab the Auto Pilot hash from the machine manually, but without going through the entire OOBE process and device reset. This method will also allow you to hit multiple machines as it will append your csv file for each machine you run it on, allowing you to only have to do the import process once instead of after each run.
Preparation
There are 2 files we need to create / download and place on a removable USB drive. First we need to download the latest Get-WindowsAutoPilotInfo from the PowerShell gallery
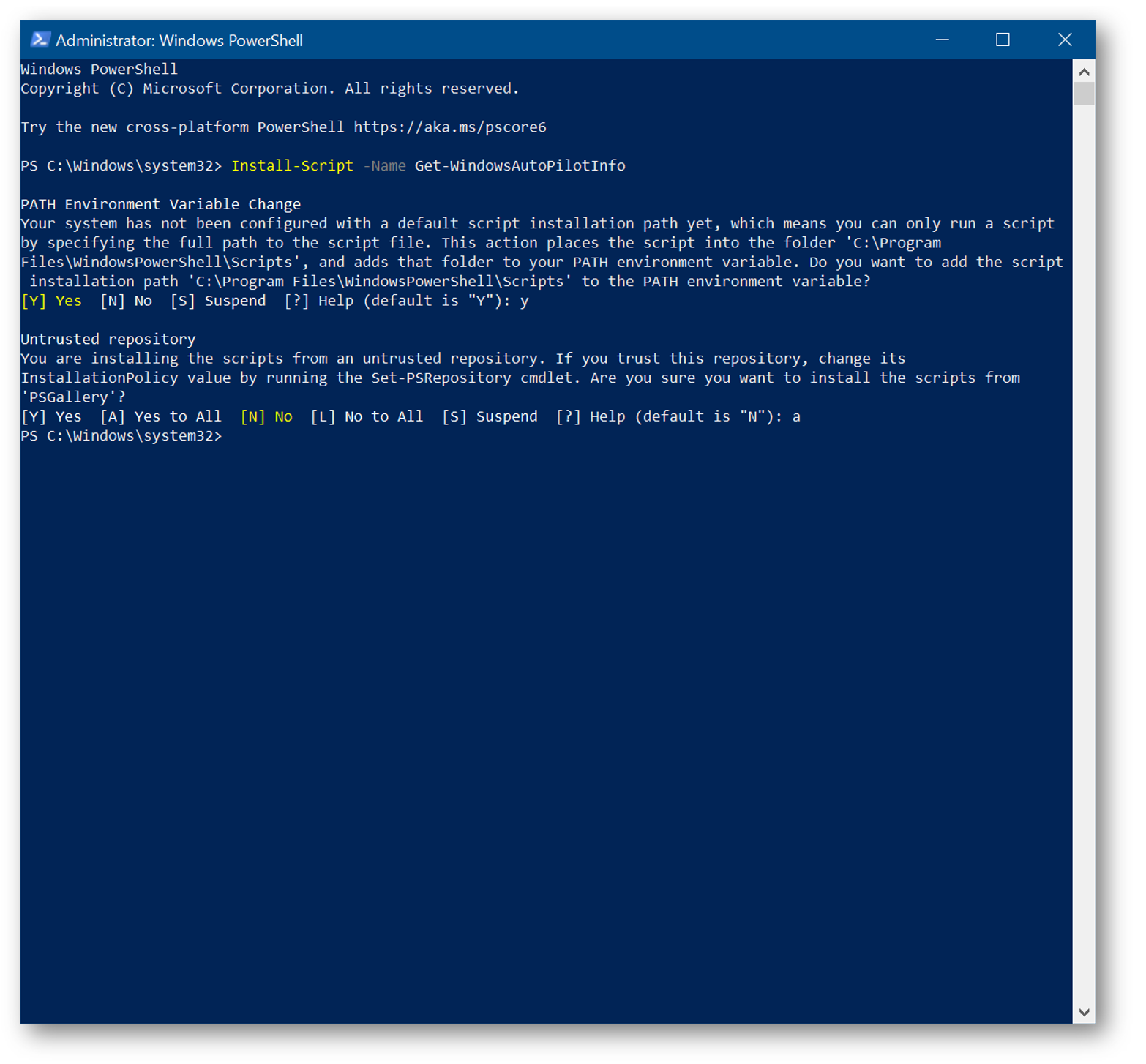
On another machine open PowerShell with elevated privileges and run Install-Script -Name Get-WindowsAutoPilotInfo
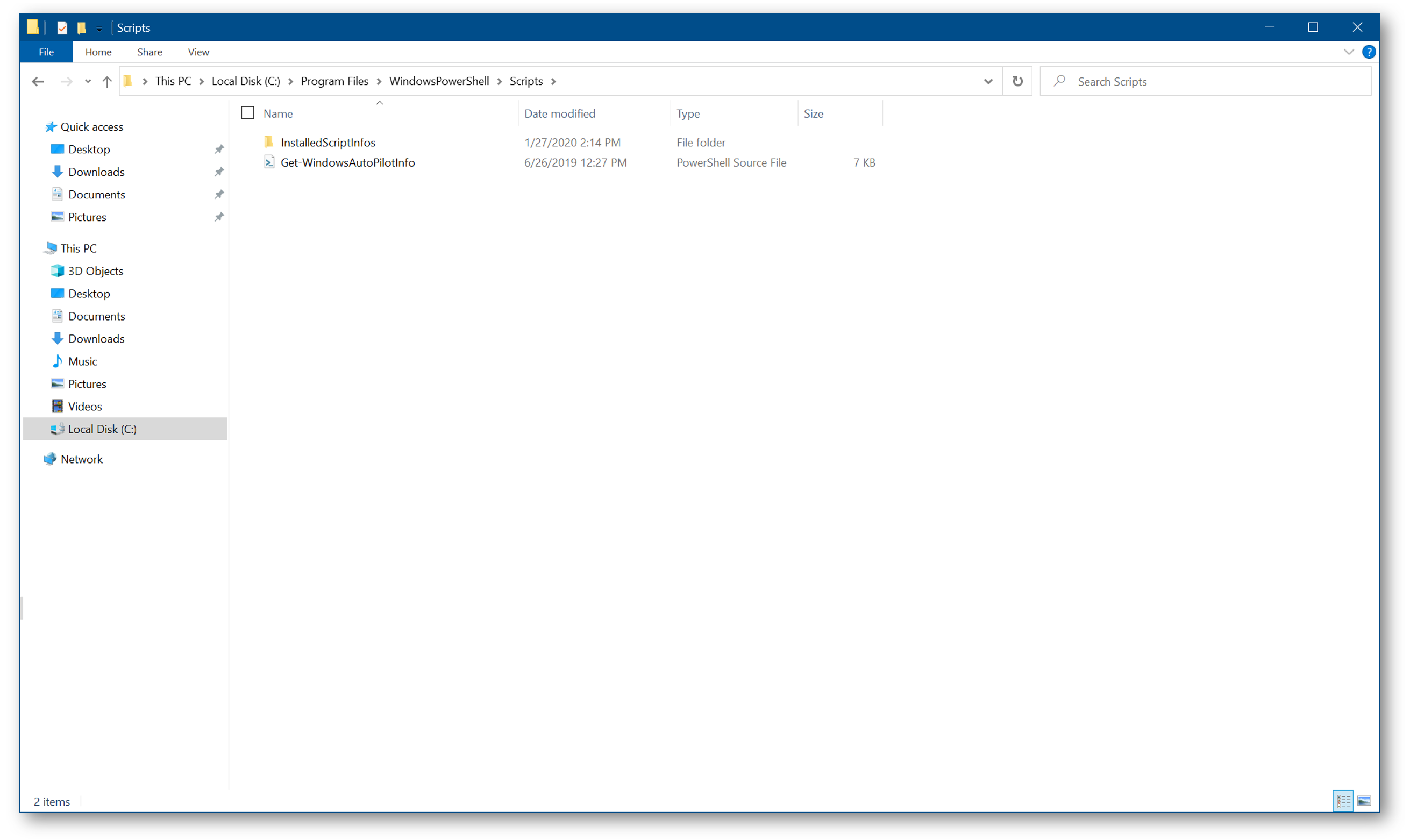
Next, navigate to C:\Program Files\WindowsPowerShell\Scripts and copy the Get-WindowsAutoPilotInfo.ps1 file to your USB drive
Next create a .CMD file with the script block below. You can simply open notepad, paste the text below, and save it as GetAutoPilot.CMD
@ECHO OFF echo Enabling WinRM PowerShell -NoProfile -ExecutionPolicy Unrestricted -Command Enable-PSRemoting -SkipNetworkProfileCheck -Force echo Gathering AutoPilot Hash PowerShell -NoProfile -ExecutionPolicy Unrestricted -Command %~dp0Get-WindowsAutoPilotInfo.ps1 -ComputerName $env:computername -OutputFile %~dp0compHash.csv -append echo Done! pause
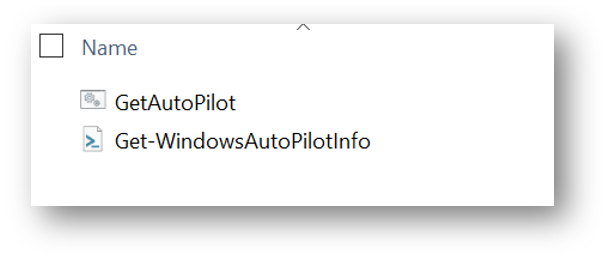
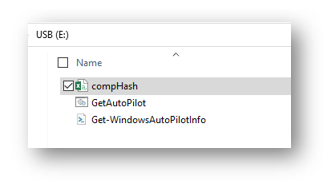
Your USB drive contents should look like the following:
Getting the Hash Without Going Through OOBE
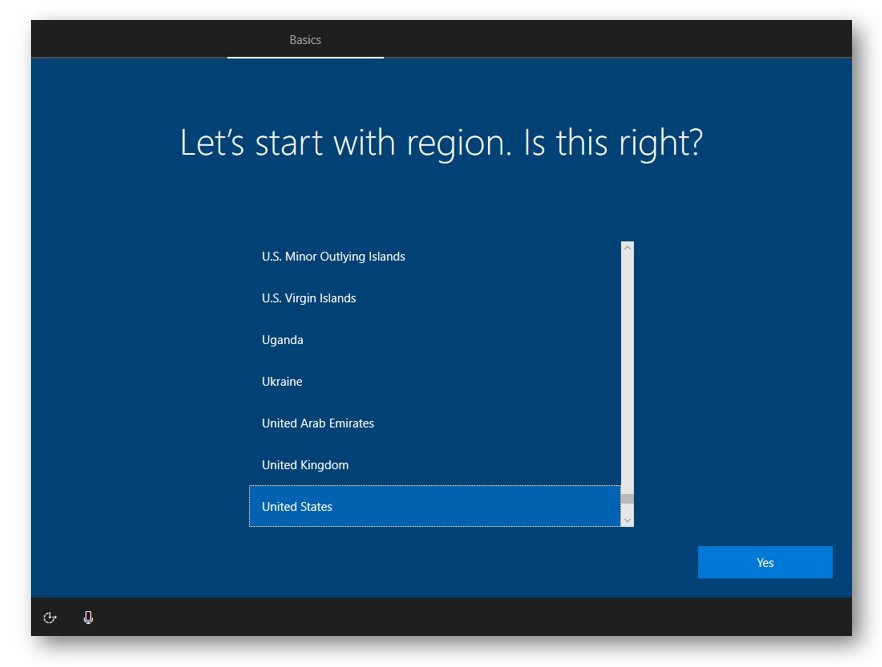
Now on your new computer, attach your USB drive to it. We don’t need to boot from the USB, we just need it to be available for us to use. When we first turn on the computer we should be greeted with the region information or something similar. This means we are in the out of box experience.
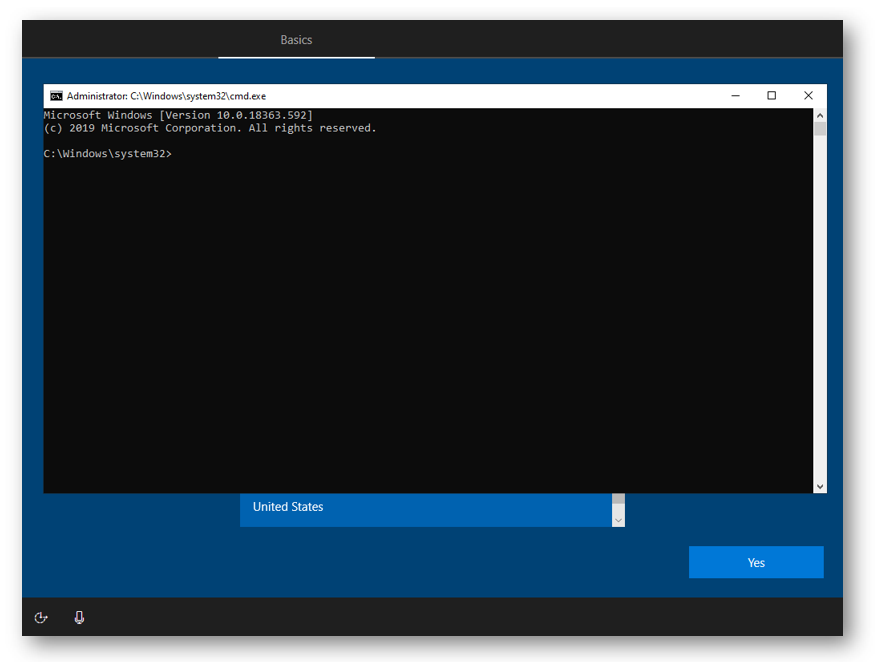
To bring up the Command Prompt, press Shift + F10 on the keyboard
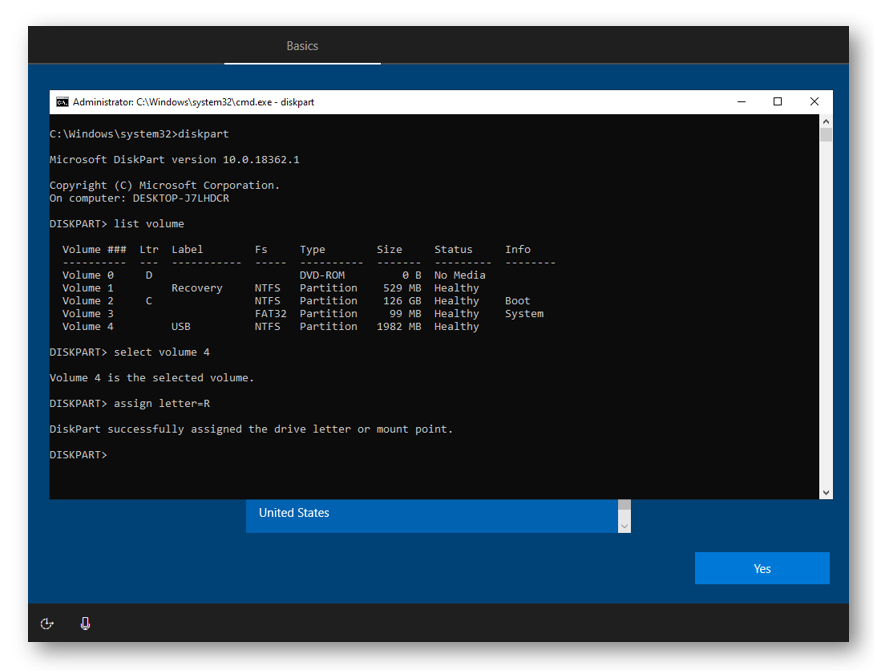
Next, we need to figure out the drive letter for our USB drive. Enter DISKPART and then list volume. In my example, my USB drive did not get a drive letter so I will select my USB volume (volume 4) by running select volume 4, and then assign it drive letter R by running assign letter=R
NOTE: Most often your drive will automatically be assigned the letter D. If this is the case you can skip this part and proceed past the DiskPart portion
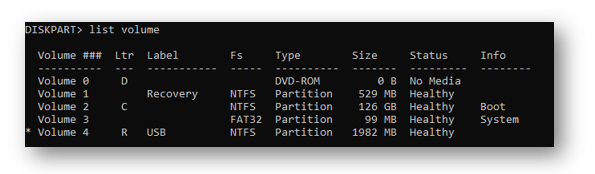
By running list volume again I can now see my USB drive has the letter ‘R’ assigned to it
Type exit to desk DiskPart
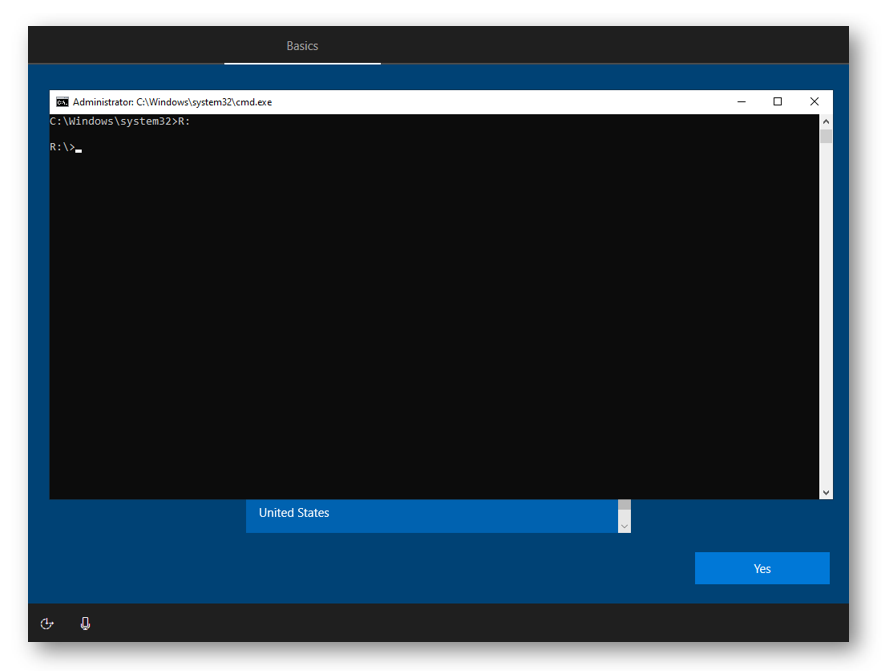
Now we can change over to that drive by simply typing the drive letter and then a colon. In my example I will run R:
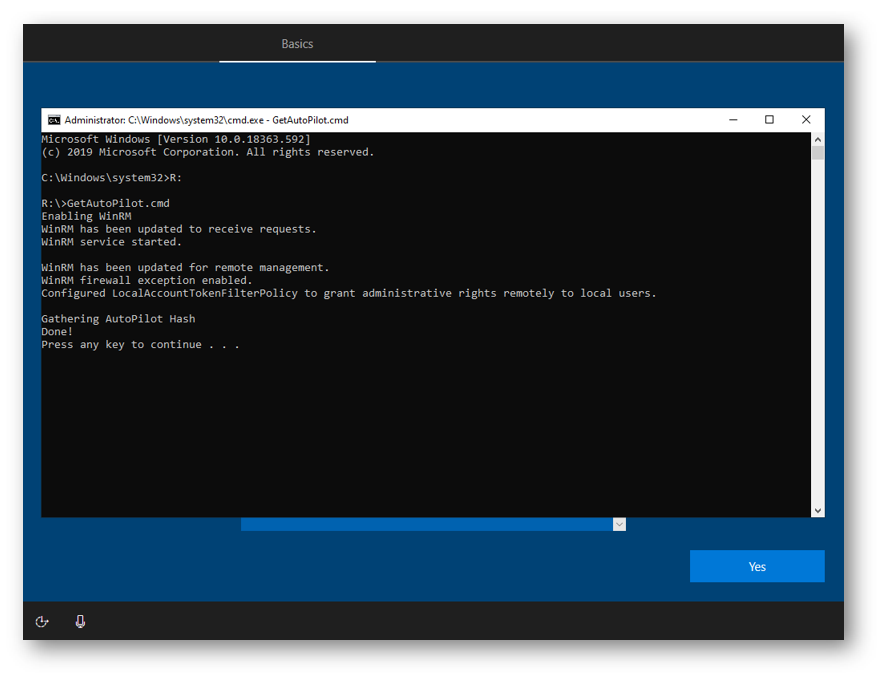
The last step we need to do is to run the CMD script. So, in your command prompt just type GetAutoPilot.cmd and then press ENTER. Once it is finished running I can simply turn off the machine until I finish importing the hash into Auto Pilot, the next time it boots it will still be at the OOBE process, but since I would have imported the hash and assigned an Auto Pilot profile, it will automatically go through the Auto Pilot process.
If we were to plug the USB back into our main machine we can now see there is a CSV on there called compHash, and it contains our AutoPilot hash for our machine. We can either upload this into our Auto Pilot in Azure, or run this on other machines as it will keep appending the csv file.

My name is Bradley Wyatt; I am a 5x Microsoft Most Valuable Professional (MVP) in Microsoft Azure and Microsoft 365. I have given talks at many different conferences, user groups, and companies throughout the United States, ranging from PowerShell to DevOps Security best practices, and I am the 2022 North American Outstanding Contribution to the Microsoft Community winner.
20 thoughts on “Get a New Computer’s Auto Pilot Hash Without Going Through the Out of Box Experience (OOBE)”
You could also skip the diskpart part, by opening a cmd and running explorer.exe.
You can also access settings, and other gui features.
Nice work, Brad! I thoroughly enjoy your blog. Keep it up…
I’ve been using that CMD/POSH trick in OOBE with great success lately, but I prefer to use the “Upload-WindowsAutopilotDeviceInfo” script https://www.powershellgallery.com/packages/Upload-WindowsAutopilotDeviceInfo/1.1.0
it skips the need to save the hw hash back to the usb and then upload it to my Azure portal. The above script lets you immediately upload the hw hash to a tenant you specify, assign it to a AutoPilot Group, and also assign it directly to a user. I’m too lazy but I am sure you could automate that and just have a couple pre-made scripts for each AP group/profile on a USB stick.
I then use Dynamic groups to scoop up the devices from those AutoPilot groups, use that group to assign AP profiles and other things like default settings and apps. Saves a lot of clicks.
You can also verify your AP enrollment status during OOBE if you press the Win key 5 times.
The script has been updated….
set-executionpolicy bypass
install-script get-windowsautopilotinfo
get-windowsautopilotinfo -online
Why are you Enabling WinRM
the script seems to work just fine with remoting
Hi,
for find out a drive letter for USB, there is a way easier solution, just type notepad in cmd, then click open, there you can see all drives connected to computer 🙂
ps. Your script and solution is great!
Just want to note a fun little snafu I got with HP EliteBook 840 G7 laptops. I had to boot it twice or I would get Null string errors.
This was EXTREMELY helpful. Thank you very much for the explanation and CMD script.
This saved alot of time. confirmed to be working in 2021.
Cheers brad.
Has anyone run this in a machine where Win 10 21H1 is pre-installed? (In OOBE of course). I get a powershell error message, too long to post here. I am running the latest Get-Windows AutoPilotInfo.ps1 file from Microsoft (version 3.4 I believe). The script works fine on other machines with older Windows versions, but this is the first time I run it on a machine with 21H1. The first line of the error message says “You cannot call a method on a null-valued expression”
It appears that the cmd file needs an update? I was able to get the hash using a manual method of Powershell commands, but not when I run the GetAutoPilot.cmd file.
As of the time of writing, the script is functioning properly.
To proceed successfully, you should navigate past the region selection screen and move forward to connecting to a network. I stoped right before choosing the type of account (Personal or Business).
When I had to choose the type of the account , I pressed shift+F10 or shift+FN+F10 and proceeded as mentioned in the article
update to this. you can download the script directly to the PC during the OOBE with out the need of a USB.
Boot the laptop to the Out of the Box experience.
go through the setup and get it connected to the internet and let it download updates and restart the OOBE
Press Shift f10 to get to the command prompt. note you may also have to press the fn key on some laptops.
enter the following line by line in the command prompt.
PowerShell.exe -ExecutionPolicy Bypass
Install-Script -name Get-WindowsAutopilotInfo -Force
Press y to allow the script to install
Set-ExecutionPolicy -Scope Process -ExecutionPolicy RemoteSigned
Get-WindowsAutopilotInfo -Online
really very good information, it is really helpfull for the extraction of hardware hash for the autopilot process.
Thanks for putting this together mate.
Still working! Thanks for posting!
Great post. Thanks for sharing !!
It has been four years and this still stands out as a gem. Thanks for this Brad. I was wondering if there is a way to include/define certain Group Tag to the script upon extraction so the group tag gets added to the hash value automatically. It would be great if could help me with this.
Hi Raja,
you can achieve this by simply changing the following line of the code:
PowerShell -NoProfile -ExecutionPolicy Unrestricted -Command %~dp0Get-WindowsAutoPilotInfo.ps1 -ComputerName $env:computername -GroupTag YOURTAGHERE -OutputFile %~dp0compHash.csv -append
It will then add the group tag to the .csv file.
Great tips! I had no idea there was a way to avoid the OOBE process for getting the Auto Pilot hash. This will definitely save me time and streamline my setup. Thanks for sharing!
Great post! I really appreciated the tips on bypassing the OOBE to get the Auto Pilot hash. It’s always a hassle going through the entire setup process, and these steps will definitely make things easier for lazy admins like me. Thanks for sharing your insights!