Enable Firefox Windows Single Sign-On using Intune
Table of Contents
One reason you may want to enable Windows SSO within Firefox, is so that your users on Azure AD or Hybrid joined machines can log into Microosft 365 services, such as Outlook, without having to re-authenticate. In this post, I will show you how to leverage Intune and custom configuration profiles to configure Firefox to enable Windows SSO.
Prerequisites
- Firefox ADMX file located here
- Intune
- Mozilla Firefox version 91 or newer
- Intune Administrator
- Test Machine with a valid Intune License
Create the Policy
- Navigate to the Intune admin portal
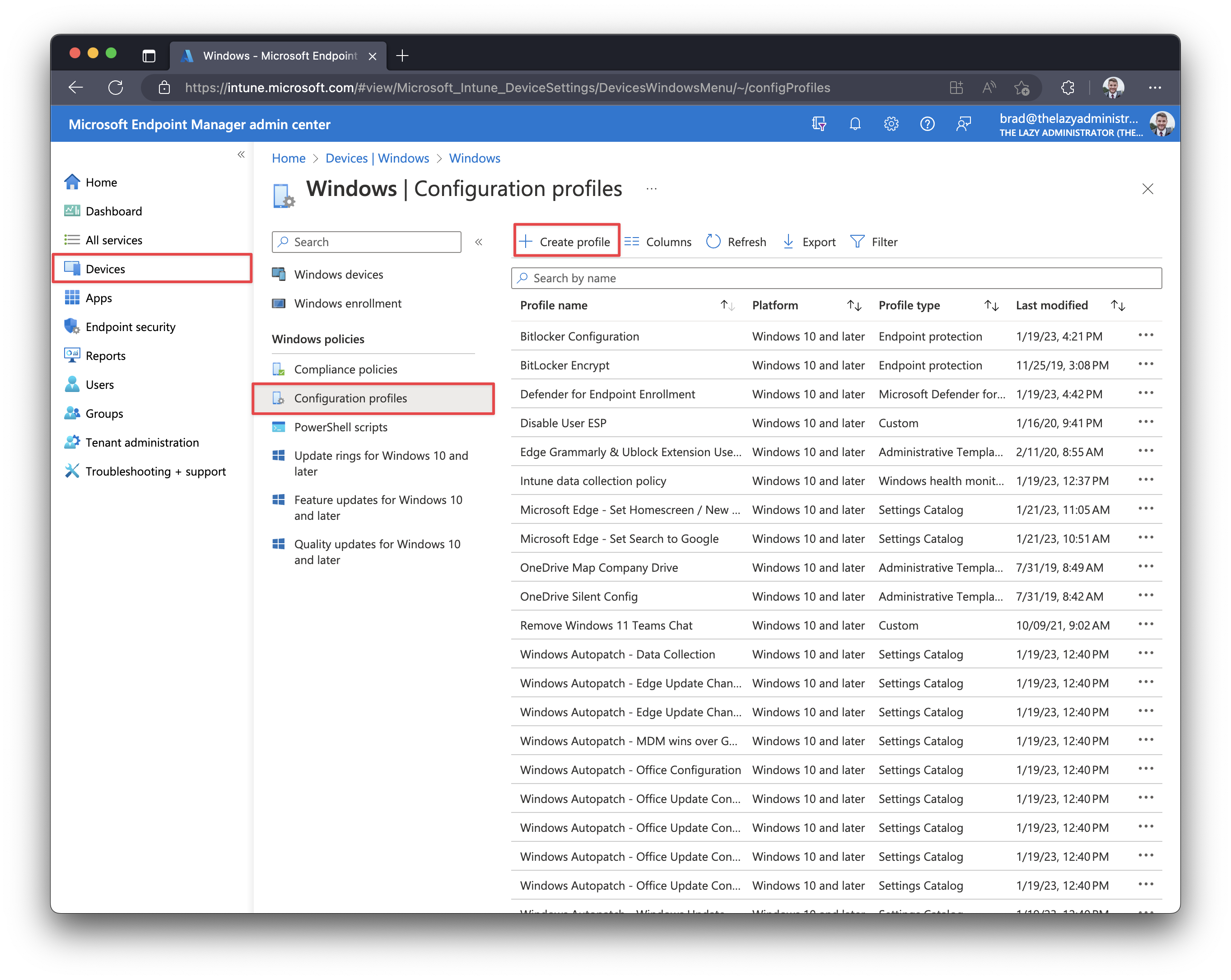
- Go to Devices > Windows > Configuration profiles > + Create profile
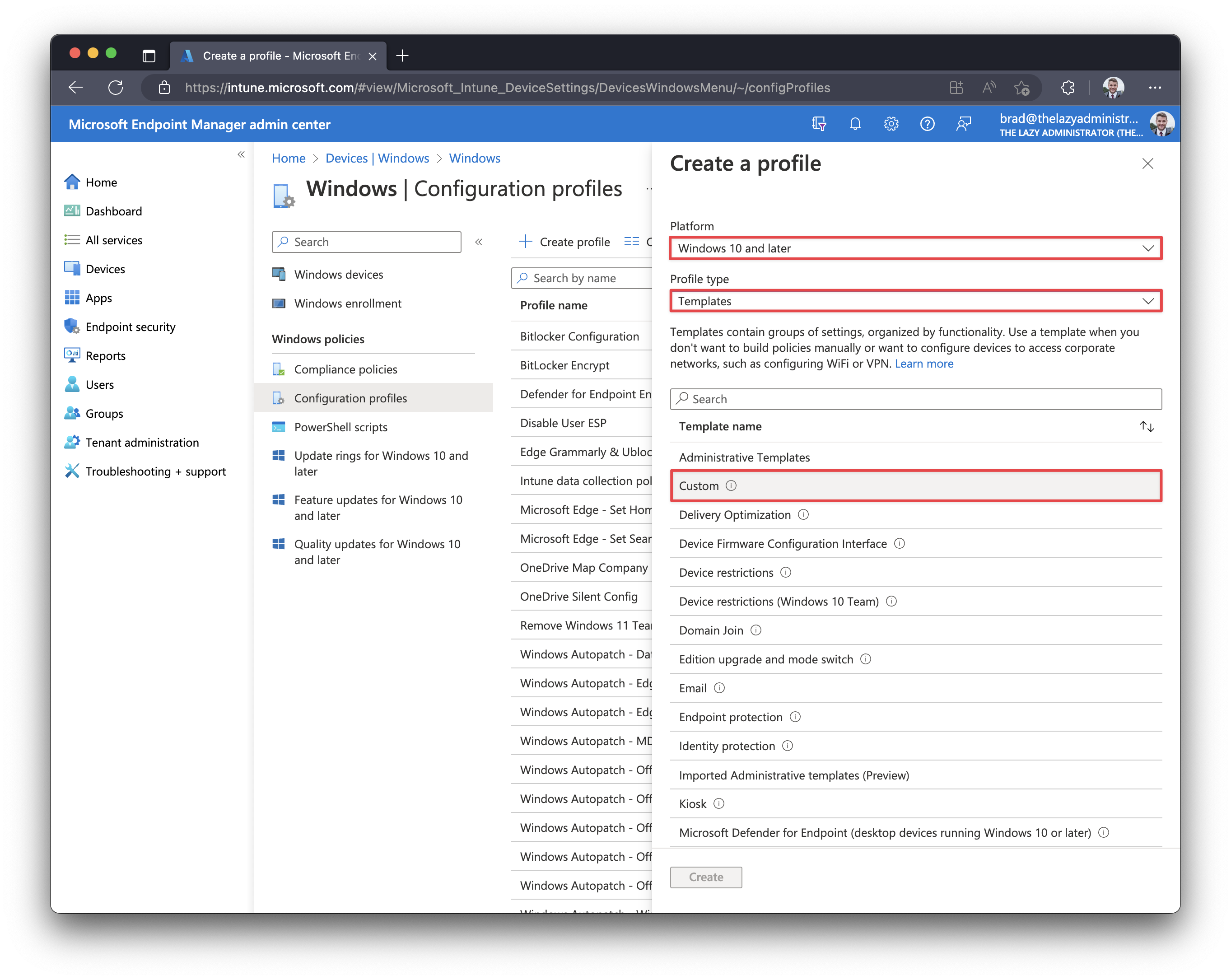
- Under ‘Platform‘ select Windows 10 and later. For ‘Profile type‘ select Templates, and then select a Custom template.
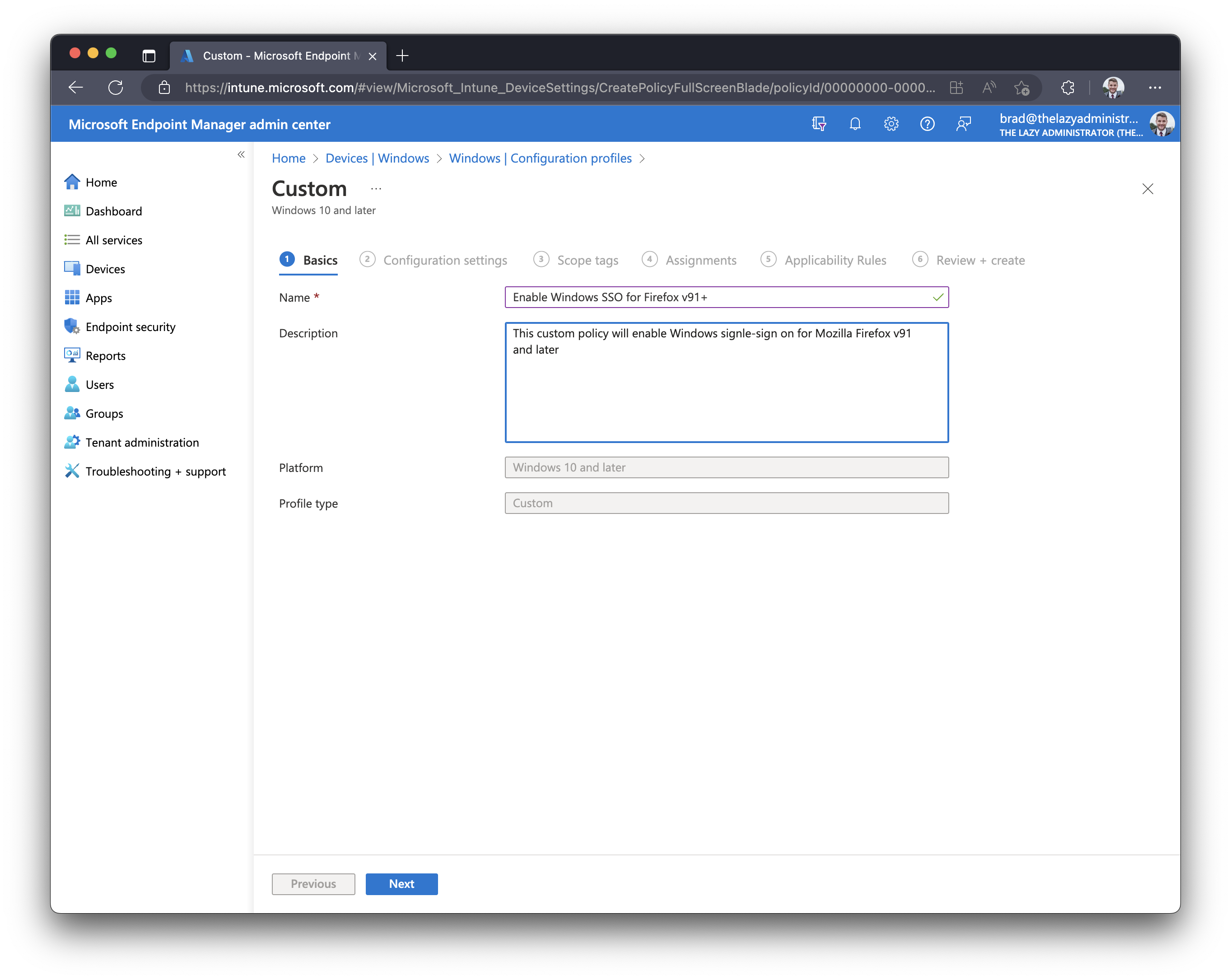
- Give you new configuration policy a good name and description so other administrators will understand what it does without having to view the configuration policy itself.
- If you have not done so already, download the most recent Firefox ADMX files from here. Then, open the firefox.admx file in a notepad or VS Code and copy the contents for the next step.
- Enter the following items
Name Ingest Firefox ADMX Description Ingests Firefox ADMX Files v4.7 OMA-URI ./Device/Vendor/MSFT/Policy/ConfigOperations/ADMXInstall/Firefox/Policy/Firefox Data Type String Value [copy the contents of firefox.admx] 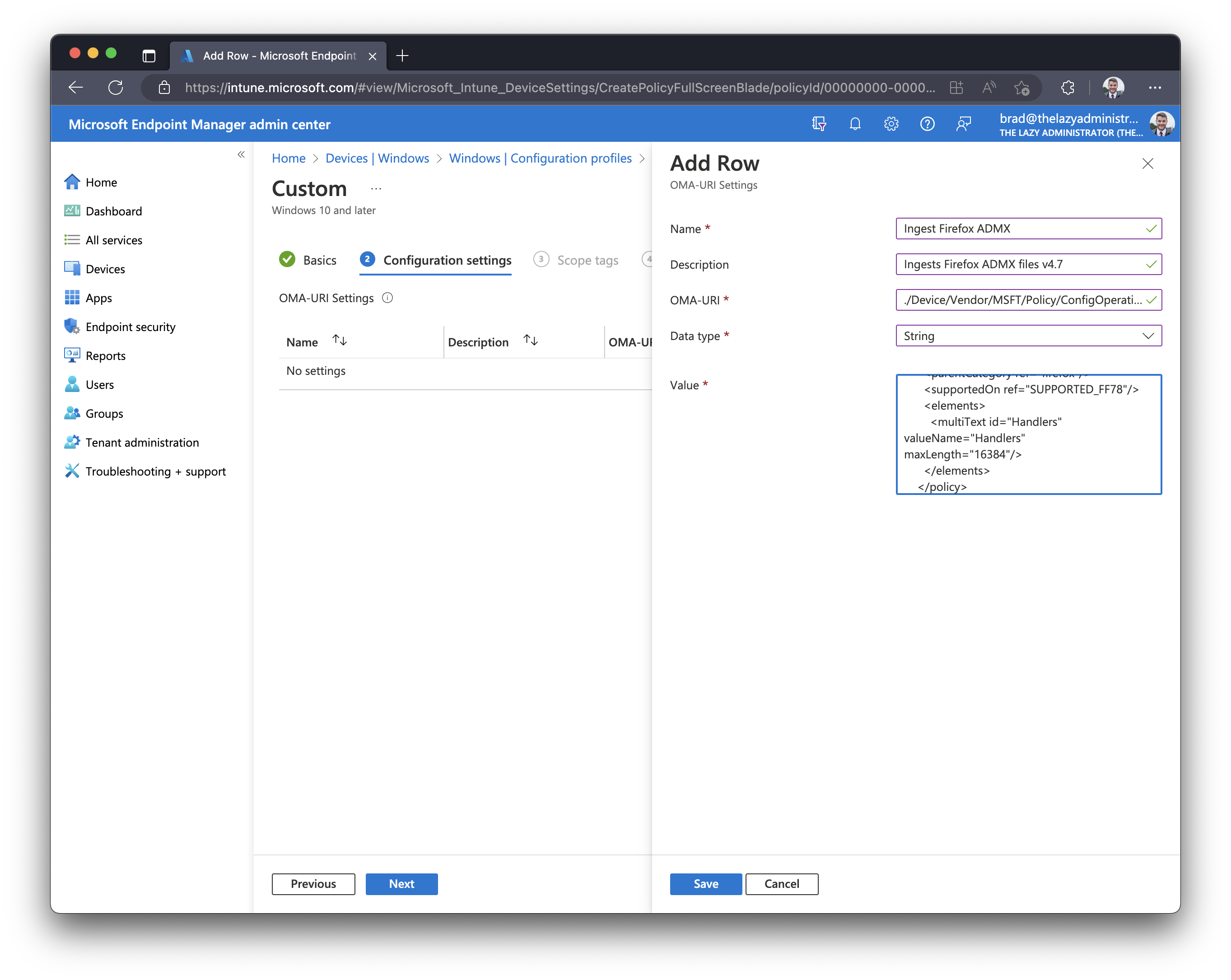
- Next, create a new OMA-URI setting using the following information
Name Windows SSO Description Firefox will use credentials stored in Windows to sign in to Microsoft, work, and school accounts. OMA-URI ./Device/Vendor/MSFT./Device/Vendor/MSFT/Policy/Config/Firefox~Policy~firefox/WindowsSSO/Policy/ConfigOperations/ADMXInstall/Firefox/Policy/Firefox Data Type String Value <enabled /> 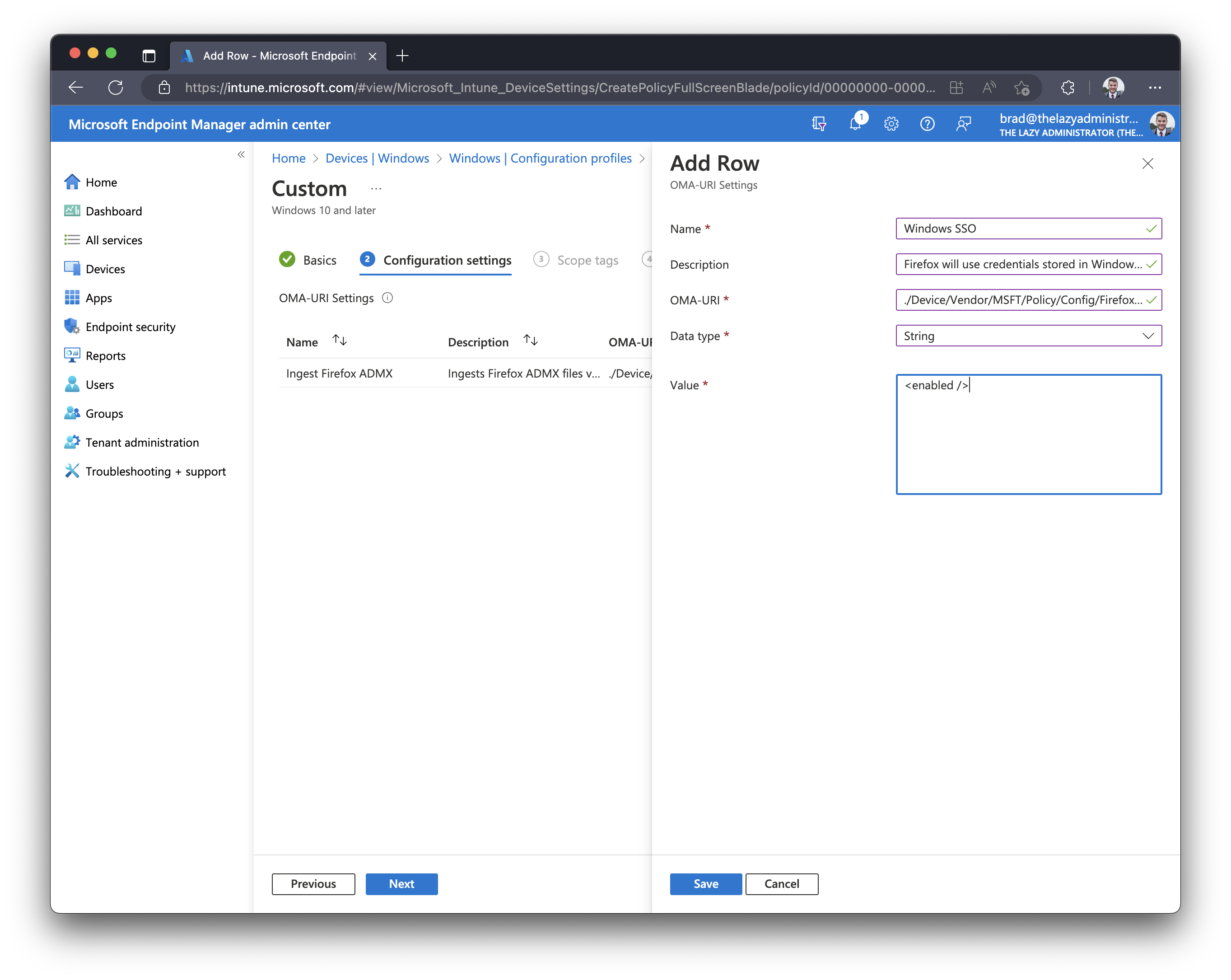
- Once finished, you should have two new settings. Click Next
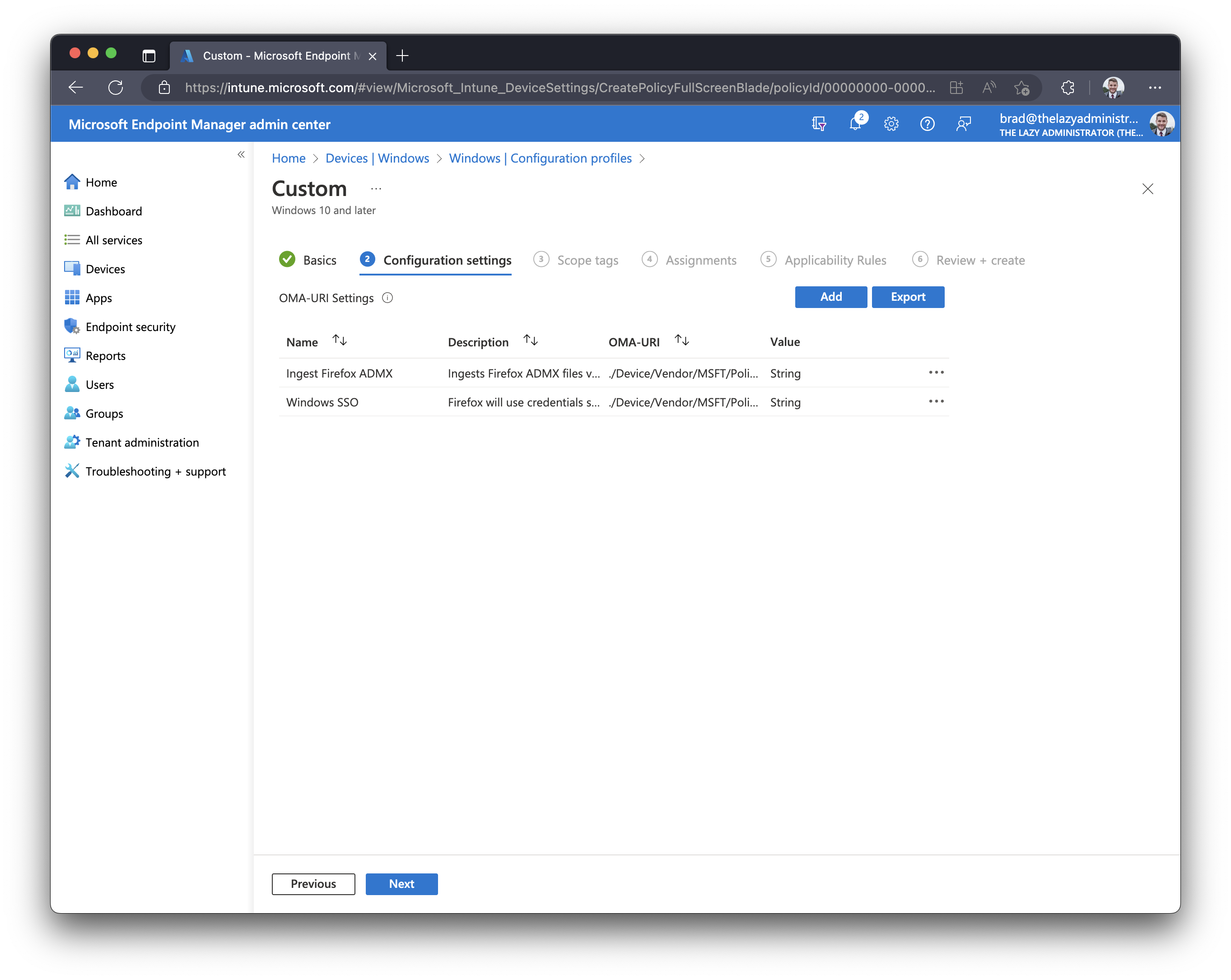
- In the Assignments tab, assign the new configuration policy to a group, all users or all devices. In my example, I applied it to all of my users.
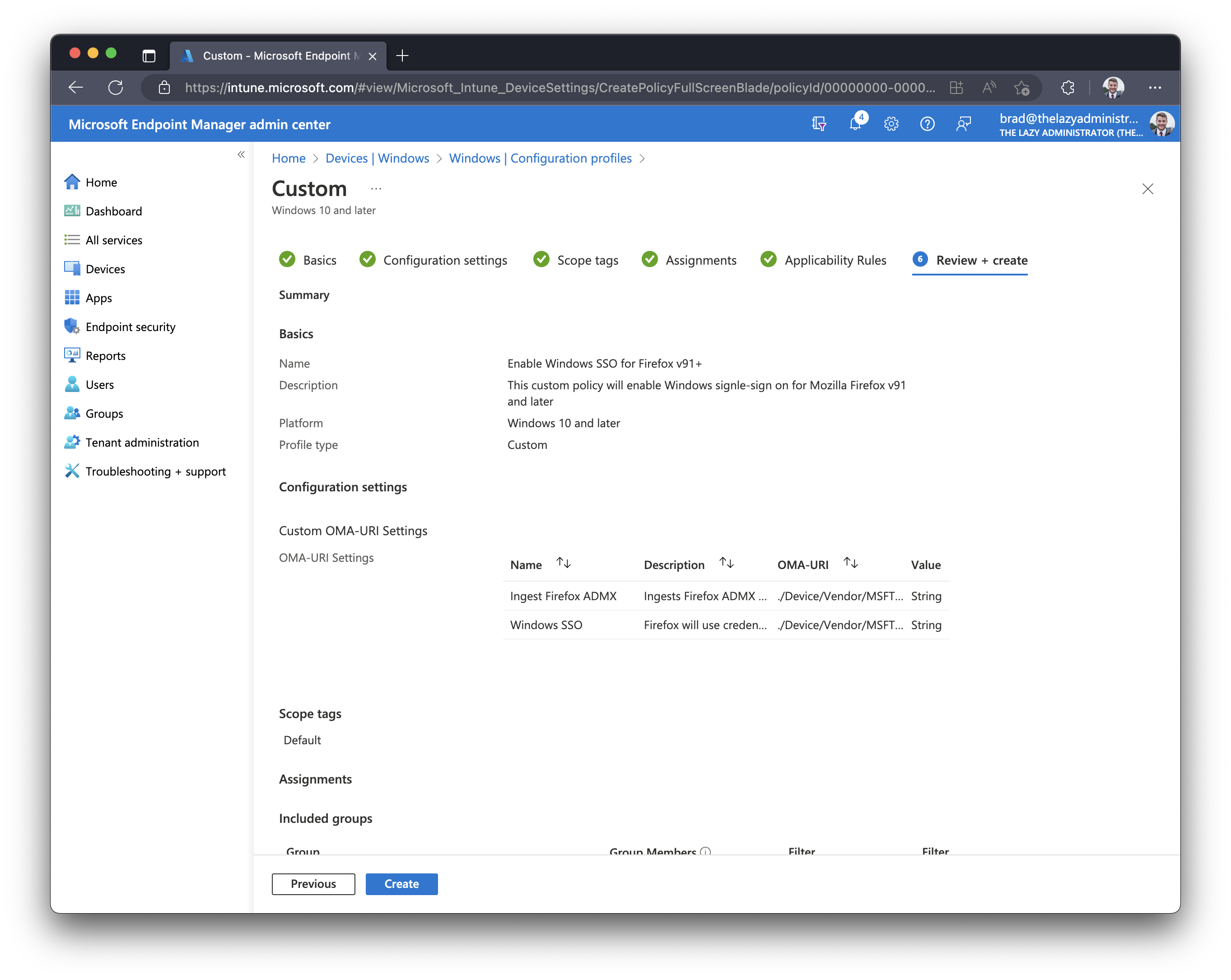
- Finally, in the Review + Create section, review your policy. If there are no further changes you are wanting to create then press the, ‘create‘ button to publish your new configuration policy.
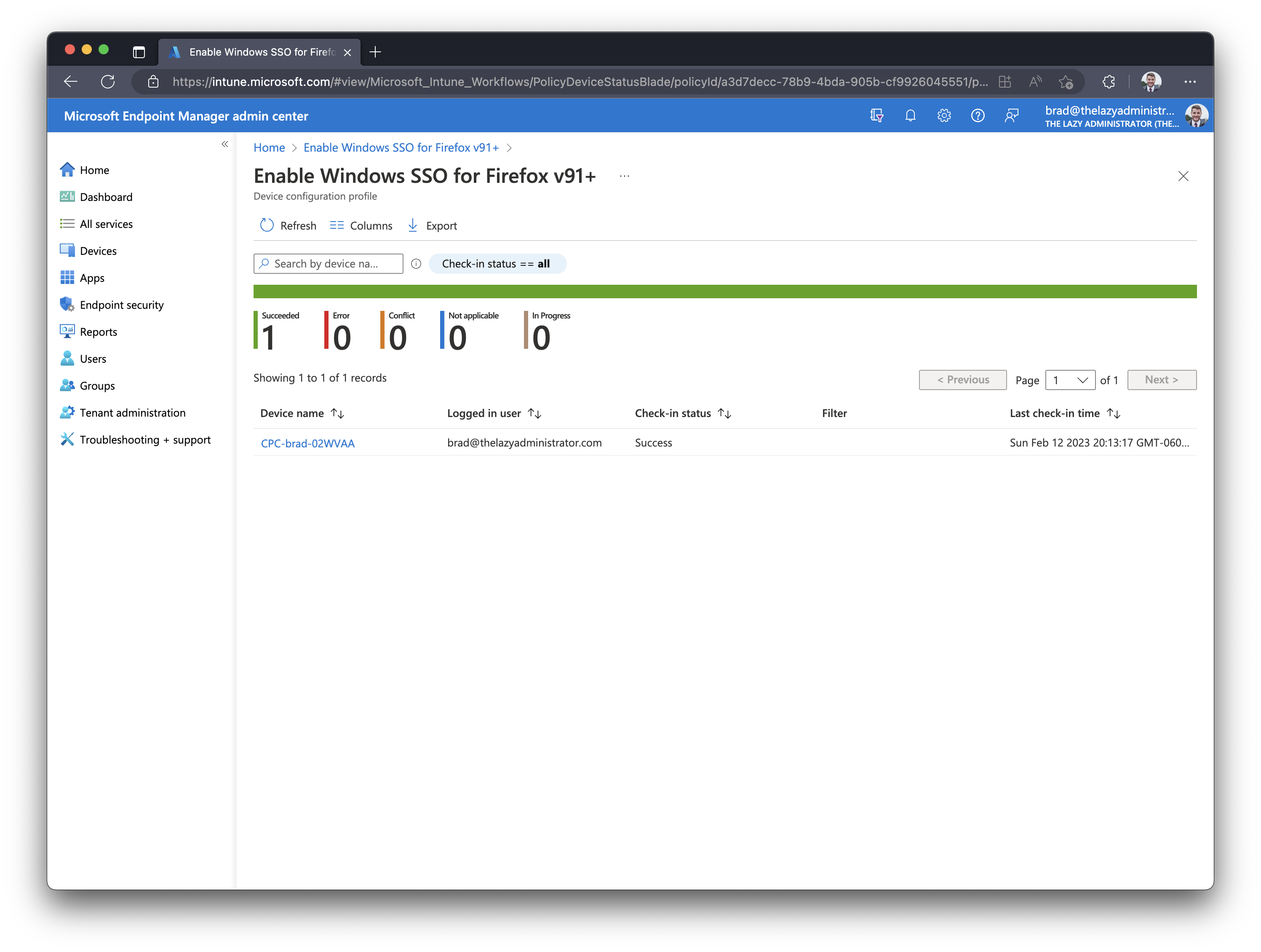
Validate
- In the Intune portal I can view the status of my configuration policy. Below I can see that it has successfully applied to my endpoint.
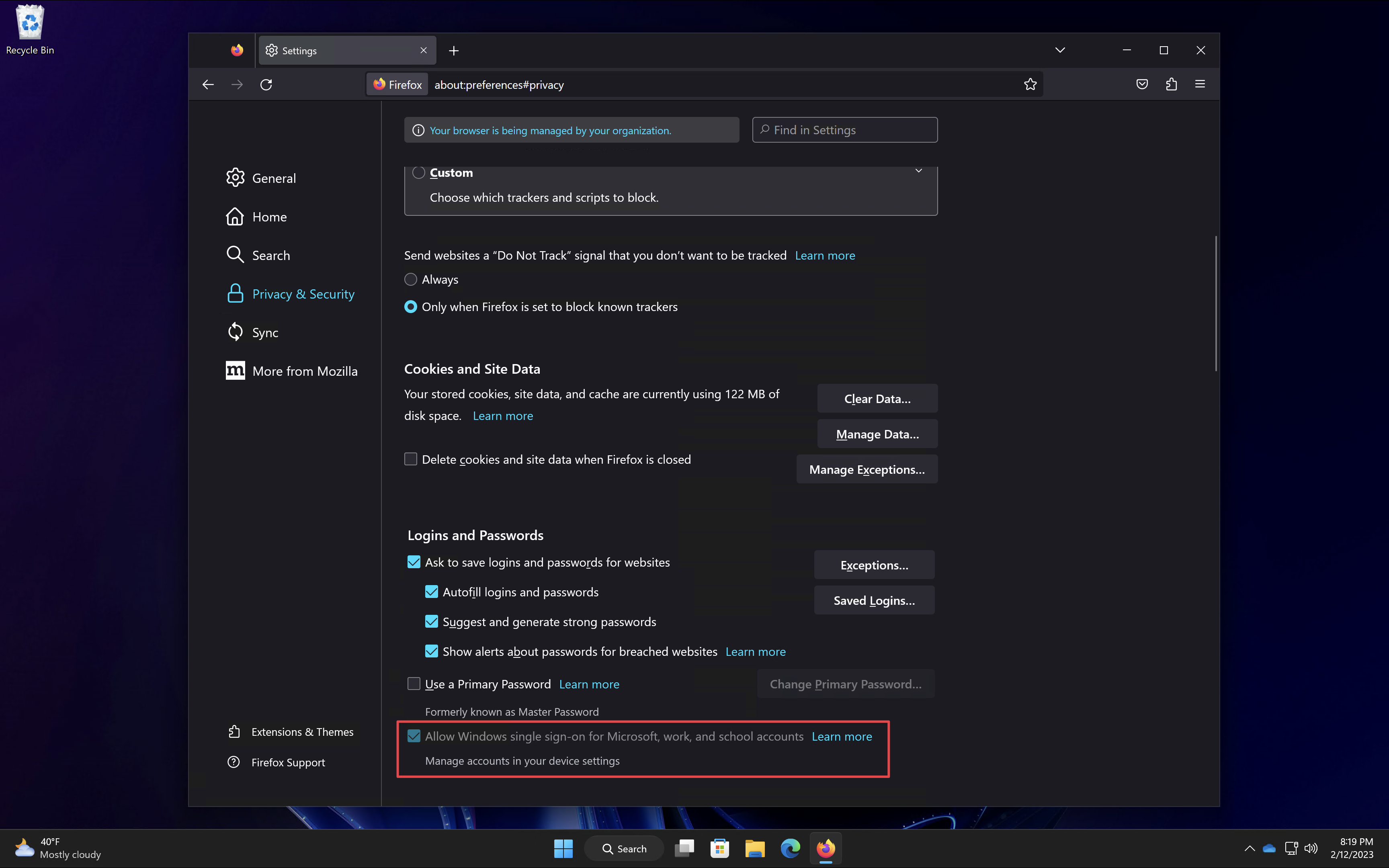
- In the Firefox settings, under Privacy & Security I can now see that the SSO setting is not only enabled, its also managed.
- I can test this out by going to login.microsoftonline.com and instead of prompting for credentials, it will automatically sign me in.

My name is Bradley Wyatt; I am a 5x Microsoft Most Valuable Professional (MVP) in Microsoft Azure and Microsoft 365. I have given talks at many different conferences, user groups, and companies throughout the United States, ranging from PowerShell to DevOps Security best practices, and I am the 2022 North American Outstanding Contribution to the Microsoft Community winner.
3 thoughts on “Enable Firefox Windows Single Sign-On using Intune”
Hi,
Thanks for sharing this article.
I followed your steps and I’m getting error code 0x87d1fdeb for ADMX install.. and other SSO enable option is fine – it says success. Do you have any idea what could be the problem?
Thanks,
I got an error with the OMA-URI for “Windows SSO” with the OMA-URI provided. I had to change it from: ./Device/Vendor/MSFT./Device/Vendor/MSFT/Policy/Config/Firefox~Policy~firefox/WindowsSSO/Policy/ConfigOperations/ADMXInstall/Firefox/Policy/Firefox
To:
./Device/Vendor/MSFT/Policy/Config/Firefox~Policy~firefox/WindowsSSO
I had the same issue and tried adjusting the OMA-URI as per your instructions, and can confirm that it works.
Thanks.